What do the words Armada, DD4BC and Lizard Squad mean to you? Nothing? Well I’m afraid, it’s time they did. That’s because they are all hacking groups that have secured worldwide notoriety for making millions of dollars from ransomware, as many councils will know only too well – if they admit it or not.
It’s a simple business model: Send a ransom letter explaining that the cyber attack they’ve set to run on your network will stop if you pay a ransom of bitcoin. And for those who don’t have a bitcoin account, they even explain how you set one up.
These groups are famous for their attacks. And it’s tempting to pay the ransom and think that the problem will go away. That’s usually when things get worse. Rather then stop the attack, the hacking group will step it up causing havoc very quickly. And if you ignore the ransom request for £1m then things can escalate quickly, as Lincolnshire County Council found out when they were a target some months ago.
As you can imagine the efforts of these organised groups have got them into hot water and arrests have been made. Thankfully this effectively shut down groups like Lizard Squad at the end of last year.
That was a significant moment for ransom attacks. It marked a turning point and the global landscape for attacks slowed.
That was until the beginning of May when our Emergency Response Team detected a exponential increase in the number of ransom letters being sent. They claimed to be from Amada Collective. They all had all the hallmarks of a genuine threat. But something didn’t quite add up. Namely that when they were outed by security specialists they switched persona and became Lizard Squad. There were other red flags too.
Firstly the deadlines set in the letters came and went without any attack taking place. When a second tranche of letters were sent to different targets, the suspicion that something strange was going on was confirmed.
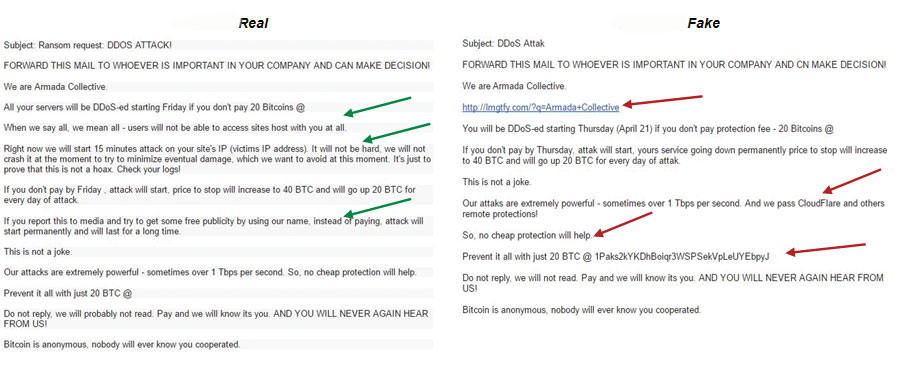
When compared to ones we’d seen before, there were subtle differences to the way the notes were written. This allowed our team to conclude the letters were bogus. To the untrained eye you’d find it hard to tall. But once the differences in approach are pointed out it’s obvious.
 Before we go through the nuances, it’s worth explaining why anyone would go to such lengths. Essentially it’s about playing on the uneducated in the name of greed. These unscrupulous impostors have no intention of running a cyber attack on your network. In fact they won’t even run a small attack to test you. Instead they play on panic. Fear that you don’t want to expose any citizen data through lapse in security, and the hope that you will Google the words Lizard Squad, and buy bitcoins as you jump to conclusions.
Before we go through the nuances, it’s worth explaining why anyone would go to such lengths. Essentially it’s about playing on the uneducated in the name of greed. These unscrupulous impostors have no intention of running a cyber attack on your network. In fact they won’t even run a small attack to test you. Instead they play on panic. Fear that you don’t want to expose any citizen data through lapse in security, and the hope that you will Google the words Lizard Squad, and buy bitcoins as you jump to conclusions.
Media interest in ransom attacks has heightened in the last six months. And given around one in three organisations has experienced a ransom attack it’s easy to see why a quick search online would lead many to think the note was genuine.
But that’s raises real concerns for me. It’s very possible that companies, charities and government organisations receiving these fake notes, most likely for the first time, will hand over the cash. As a result, they will be drawn into a false sense of security. If we pay we survive.
Of course, the reality is that it’s only a matter of time before we see a genuine group establish itself. And when it does, it will mean business. Thinking you will be able to pay your way out of it because it worked before is misguided.
What precautions should you take then? There are a number of indicators that will help you spoke a fake, but also some rules to follow when managing ransom threats in general
Starting with spotting a fake, there are five watch outs:
1. Pride. Real hackers prove their prowess by running a small attack while delivering a ransom note. If your network activity changes then it’s probably genuine.
2. Money. Fake hackers request differing amounts of money. Armada Collective normally ask for 20 bitcoin. Low bitcoin ransom letters are most likely from fake groups. They hope that their pricing is low enough that organisations will pay rather than seek professional assistance.
3. No formal identity. Fake hackers don’t link you to a website because they don’t have one nor do they have official email accounts. Both good signs they are not a formal group.
4. Non-specific approach. Real hackers tend to attack a single sector at a time. Fake hackers target indiscriminately.
5. Spot the difference. The image shows that there are subtle differences between a real and a fake ransom note. It takes practice to spot the differences so if in doubt send it to a specialist to review.
Let’s now look at how to deal with an attack:
1. Check before you do anything. Whether you think it is real or not, find an expert who can tell you how you to protect your network before you do anything. The minute you engage with a ransom group you’ll open up an attack you could never have planned for.
2. Understand the threat. There’s lots written about training your teams on security risk. Make sure it isn’t a tick box exercise. You should be telling employees to check email spam filters regularly so genuine ransom notes are not missed. Many organisations have unwittingly ignored the genuine threats because they hadn’t seen the email. The result is that the attack steadily intensifies and become unmanageable.
3. Employ an ex-hacker. This will be controversial for many companies and especially councils, but many are warming to the idea – employ an ex-hacker who can help you identify the risks. If you think this is too high risk then work find a partner who is employing one. They can spot attacks on the horizon long before they become a big problem and help you tighten up your security in the right way.
When you know the signs to look for, planning and managing attacks becomes easier. Granted it’s not easy to do but you can be more focused and effective if you have this understanding. Bottom line, you can protect your citizens their confidential information, your employees, and your public reputation more successfully.
Adrian Crawley is regional director for EMEA at Radware.












